The only system which is truly secure is one which is switched off and unplugged, locked in a titanium lined safe, buried in a concrete bunker, and is surrounded by nerve gas and very highly paid armed guards. Even then, I wouldn’t stake my life on it
MobSF
MobSF is a tool for doing a basic automated penetration test on a mobile app.
Here's how to get it up and running:
Install Docker CE Desktop
Start Docker and go through its setup.
Check whether Docker is running via its icon in the macOS system dock.
Open the terminal and run
docker pull opensecurity/mobile-security-framework-mobsf. That command will pull themobile-security-framework-mobsfcontainer from DockerHub.Start your web browser and navigate to
localhost:8000(0.0.0.0:8000). If the MobSF app starts, you are good to go.Drag and drop your .IPA or .APK file into MobSF and wait for the pen test to run.
OWASP ZAP
The OWASP Zed Attack Proxy (ZAP) is another helpfull tool that can help you automatically find security vulnerabilities in web applications while being developed and tested.
Here's how to get it up and running:
- Download the installation file from OWASP ZAP
- Run the installer
- Finish the installation
For detailed information on how to set up the app use this handy guide
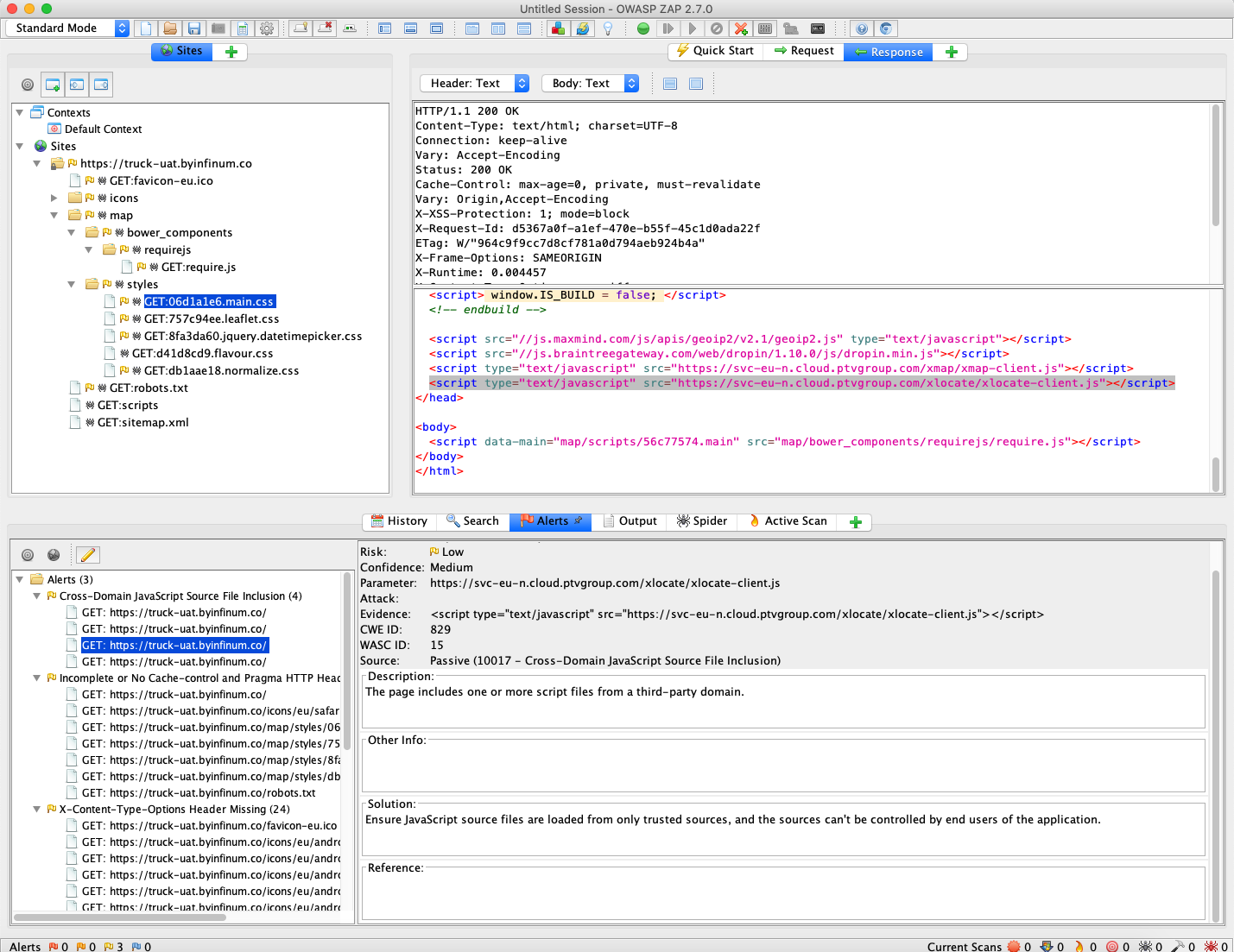 OWASP ZAP 2.7.0
OWASP ZAP 2.7.0
Objection
Objection is a runtime mobile exploration toolkit, powered by Frida. It was built with the aim of helping assess mobile applications and their security posture without the need for a jailbroken or rooted mobile device.
Features
For all supported platforms, objection allows you to:
- Patch iOS and Android applications, embedding a Frida gadget that can be used with objection or just Frida itself.
- Interact with the filesystem, listing entries as well as upload & download files where permitted.
- Perform various memory related tasks, such as listing loaded modules and their respective exports.
- Attempt to bypass and simulate jailbroken or rooted environments.
- Discover loaded classes and list their respective methods.
- Perform common SSL pinning bypasses.
- Dynamically dump arguments from methods called as you use the target application.
- Interact with SQLite databases inline without the need to download the targeted database and use an external tool.
- Execute custom Frida scripts.
If you want to know more on how to use AppMon please follow this handy guide. Information on how to patch app via terminal can be found here
AppMon
AppMon is an automated framework for monitoring and tampering system API calls of native macOS, iOS and android apps. It is .useful tool for the mobile penetration testers to validate the security issues report by a source code scanner and by inspecting the APIs in runtime and monitoring the app’s overall activity and focus on things that seem suspicious.It is based on Frida.
For more information about setup and how to's please follow this handy guide.

QARK
QARK is an easy to use tool capable of finding common security vulnerabilities in Android applications. It features educational information allowing security reviewers to locate precise, in-depth explanations of the vulnerabilities. More you can read more by following this link
Here’s how to get it up and running:
Open terminal and type following command:
pip install --user qark * or *
pip3 install --user qark
You will need to install Java on your machine, to do so just follow this link
After finding path to the QARK installation folder use this command to add that path to environment variable:
sudo nano /etc/paths
To launch
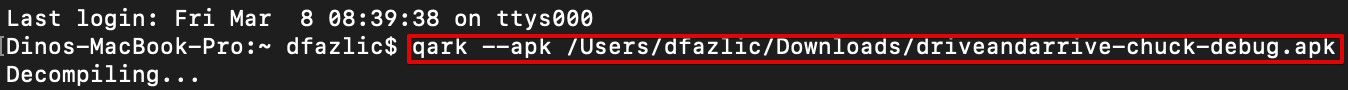
To use QARK with some app you need to download the app package Path to app file that you previously downloaded
qark --apk path
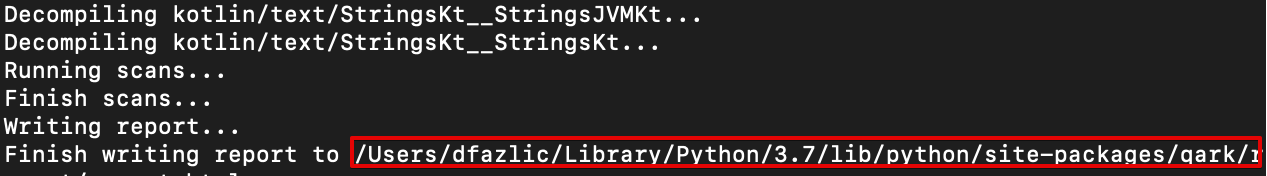
After the decompiling is finished use the generated path to find the report. To do this just copy the path from terminal and paste it to the finder/go/go to folder
You can send report to the developer along with the decompiled build you can find on your machine under:
/Users/"your user name"/build
More information about QARK can be found by following this link.