Security is a dish best served throughout the development process. Find out how adopting the Secure Software Development Life Cycle (SSDLC) protects your application from ever-evolving dangers in the digital space.
In today’s software development world, there is so much to think about: quality code, continuous integration and development, cloud environments, high performance and availability, top-notch user experience… The list goes on. However, one aspect that genuinely ties it all together is cybersecurity. Or, in this case, application security.
Why is this so important? You can have the most beautiful windows and the finest furniture in the world, but they’re of little use if the first gust of wind brings the whole building down. And as we know, the winds, tornadoes, hurricanes, and earthquakes of cyber threats show no signs of letting up.
And this isn’t just about product team responsibility anymore, it’s a legal requirement.
The Cyber Resilience Act, taking effect throughout 2026, introduces mandatory cybersecurity rules for digital products sold in the EU. It’s part of a broader push to raise digital resilience and will directly impact how products are designed, built, and maintained.
This is where the Secure Software Development Life Cycle (SSDLC) comes in. Often mentioned together with the phrase “shift left,” the methodology emphasizes the importance of integrating security practices at every phase of the development process.
From SDLC to SSDLC
Let’s start with the first abbreviation: a software development lifecycle (SDLC) is a set of rules and processes a team uses to design, develop, test, deploy, and maintain software. Some of them are standard, like waterfall or XP, but in practice, there are as many specific SDLCs as development teams worldwide.
You could probably bet that as soon as Ada Lovelace wrote the first computer program, someone started to wonder, “Hmmm, how do we formalize this?” The fact is, when we standardize a process, it tends to run more smoothly. And considering that software gets shipped by the truckload every day, those SDLCs seem to be working.
So, why would we want to shift anything anywhere?
The ‘shift left’ approach
The metaphor refers to moving a process to an earlier point in the development lifecycle, moving it left on an imagined project timeline. Some may argue that “shift left” is a buzzword or a worn-out phrase in software development, but it is essential nonetheless.
Security calls for an urgent shift left. When we implement security practices at every step of the development process, SDLC becomes SSDLC.
Almost anyone working on a development project wants to get involved earlier on in the cycle – nobody wants to finish the race last. Years ago, it was software testers; they didn’t want the aforementioned truckload of software passed on to them without prior knowledge or involvement. Changes in development culture and test automation did, to a degree, manage to get them there.
Today, security calls for its own shift left. Thus, SDLC becomes SSDLC – Secure Software Development Lifecycle.
One way to achieve this goal is to adopt a DevSecOps culture, something that teams worldwide are already doing, and with relative success. The DevSecOps methodology is based on key principles such as automation, collaboration, and continuous monitoring. As the name suggests, it involves security teams working alongside development teams and operations to bake in security practices at every stage of the process.
Microsoft’s Security Development Lifecycle and NIST’s Secure Software Development Framework can also serve as examples. These methods may not be directly comparable, but the main idea is the same – to infuse every stage of the SDLC with security thinking and introduce activities that ensure the product is resilient and robust.
The benefits of adding the “S”
A worrying statistic from CISQ and Synopsys (albeit from 2022) notes that “the cost of poor software quality in the U.S.—which includes cyberattacks […], complex issues involving the software supply chain, and the growing impact of rapidly accumulating technical debt—will total approximately $2.41 trillion.”
Of course, everyone wants, needs, and expects their applications to be secure by design and default. But let’s unpack this and illuminate what exactly you are getting by integrating security considerations into your SDLC:
- Higher code quality and reliability, less technical debt
- Early detection and eradication of security vulnerabilities and a reduced attack surface
- Faster development and cost-savings by eliminating rework
- Meeting legal security requirements to prevent fines and penalties and avoid release delays
- Protection of sensitive data and prevention of breaches
- Continuous risk management
- Incident response preparedness and quick recovery
- Long-term stability, scalability, and competitive differentiation
- Protection of reputation and ensuring customer trust
A big promise? When done right, security initiatives can indeed have that much of an impact. And it may sound like a distant dream, but achieving a secure software environment is well within reach.
OWASP SAMM as a starting point for SSDLC
We’ve mentioned a couple of “frameworks” that can serve as a basis for instilling security into your development process. However, knowing what and how to implement requires assessing the current state. It’s hard to fix anything when you’re working in the dark.
This is where the OWASP Software Assurance Maturity Model (SAMM) comes in handy. According to its creators, the model is designed to help organizations of all types analyze and improve their security posture effectively and measurably. It covers the entire software lifecycle and is adaptable to various technologies and processes, being both evolutive and risk-driven.
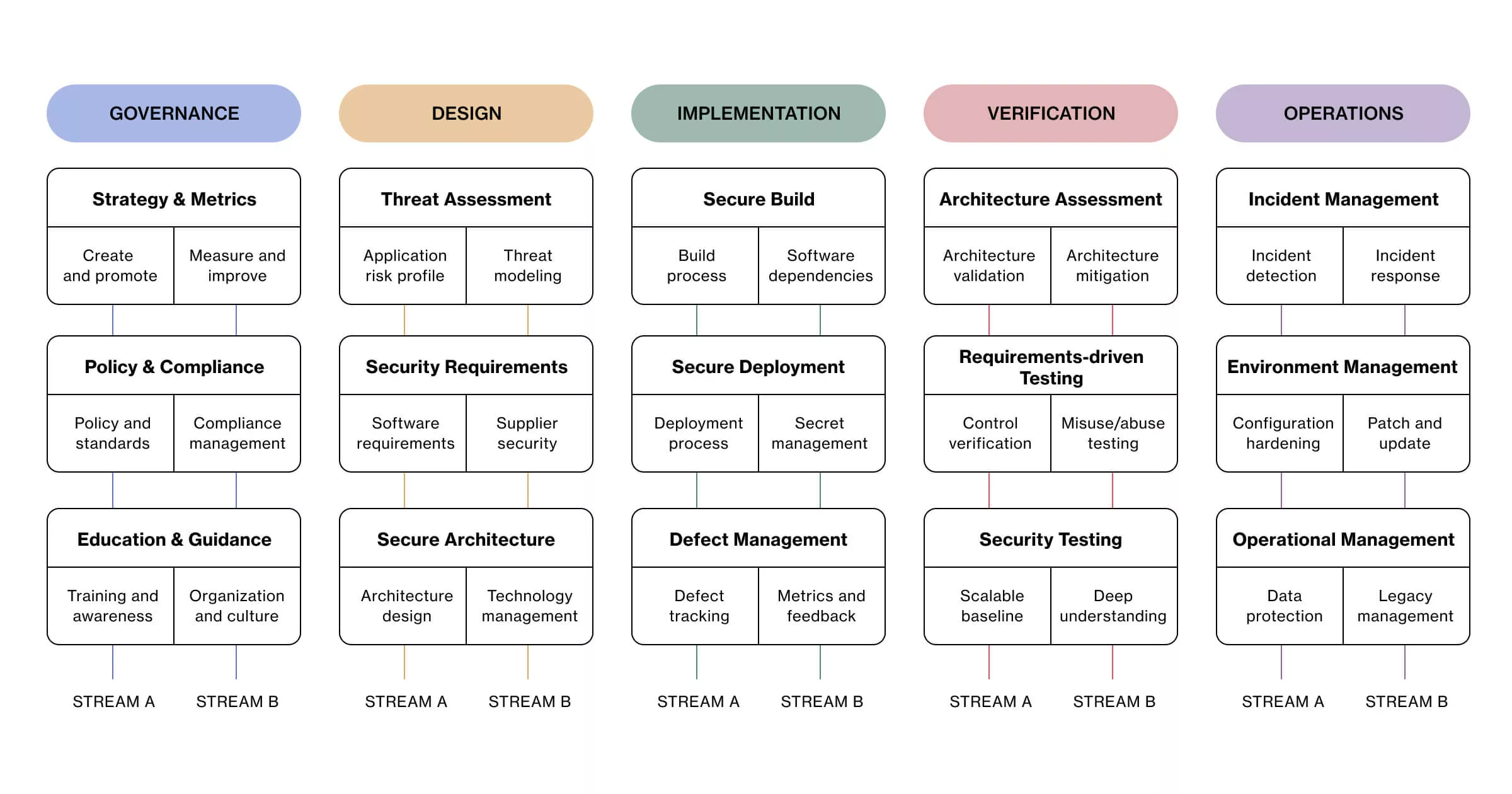
In essence, SAMM is divided into five distinct business functions, each consisting of three security practices. These practices can be scored on a 1-3 maturity scale, and voilà – you get some “measurable” indication of how much security is built into your processes.
As is always the case with software development, the whole thing is highly contextual. The goal is not to get a maximum score but to assess and minimize the security risk in relation to your industry and your product so you can gradually improve your security posture.
No one has ever built a bulletproof process, but state-of-the-art locks and guardrails are better than leaving your door completely open.
How to go about implementing the model?
Your SSDLC stages may not perfectly align with the OWASP SAMM model, but the important thing is to define what’s crucial for your particular product and business.
One of the model’s biggest benefits is that it helps your organization determine where it stands on its journey toward software assurance and what it needs to do to move to a next level of maturity.
The whole implementation process is described in OWASP’s official documentation, and it includes the following steps:
Prepare
Defining the scope of the initiative and identifying the stakeholders.
Assess
Evaluating the current practices and determining their maturity level.
Set the target
Defining which activities we want to improve and what impact this will have on the entire organization.
Define the plan
Determining a precise schedule for introducing the changes.
Implement
Implementing all the activities, considering their impact on processes, people, knowledge, and tools.
Roll out
Making all the changes visible for everyone involved through education and training; measuring their adoption.
It may seem like a lot to take in, but once you start adopting a security mindset, you see how vast the area for improvement can be. And hopefully, once you start implementing those improvements, you realize that so are the benefits.
Time to make that shift to SSDLC
Hardening software development practices is no longer a point of contention but a business and technical necessity – at least if you want to make your product stable, resilient, and long-lasting in today’s out-of-control cyber environment.
Just as a building’s strength relies on its robust steel rails rather than mere aesthetics, software security depends on rigorous, integrated security measures throughout the development lifecycle.
To make that shift left, you first need to shift security up on your list of priorities. And if you need any help leveling-up your SDLC to SSDLC, check out our cybersecurity services.